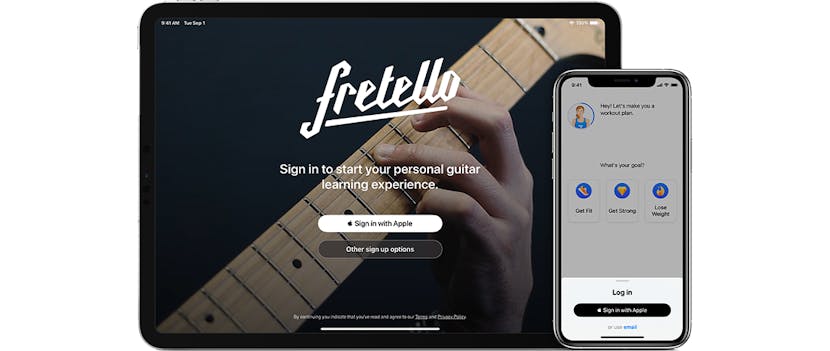
Sign in with Apple: the secure alternative
Identity fraud is one of the most rapidly growing online criminal activities. Hackers gain access to personal data by hacking into companies that collect large quantities of data. It is wise to reveal as little as possible about your identity. And Sign in with Apple makes that possible.
Read more